U.S. to Deport Venezuelans Convicted of ATM Jackpotting Attacks Using Ploutus Malware
Federal authorities are moving to deport Venezuelan nationals convicted of orchestrating ATM jackpotting attacks across the United States using the Ploutus malware. The operation, linked to the transnational gang Tren de Aragua, caused millions in losses by forcing ATMs to dispense cash on command. This case highlights the ongoing convergence of physical access attacks and sophisticated malware in the financial sector, and the cross-border dimension of modern cybercrime enforcement.
What happened
Federal prosecutors have secured convictions against Venezuelan nationals who conducted a coordinated ATM jackpotting campaign across the United States. The attackers used Ploutus malware, a specialized tool designed to force ATMs to dispense their entire cash reserves on command.
Attacks linked to Tren de Aragua, a Venezuelan transnational gang expanding into cybercrime
The operation is connected to Tren de Aragua, a notorious Venezuelan criminal organization that has expanded its operations from South America into the United States, diversifying into cybercrime alongside traditional criminal activities.
Following conviction, the individuals now face deportation as part of broader U.S. efforts to disrupt transnational cybercrime networks.
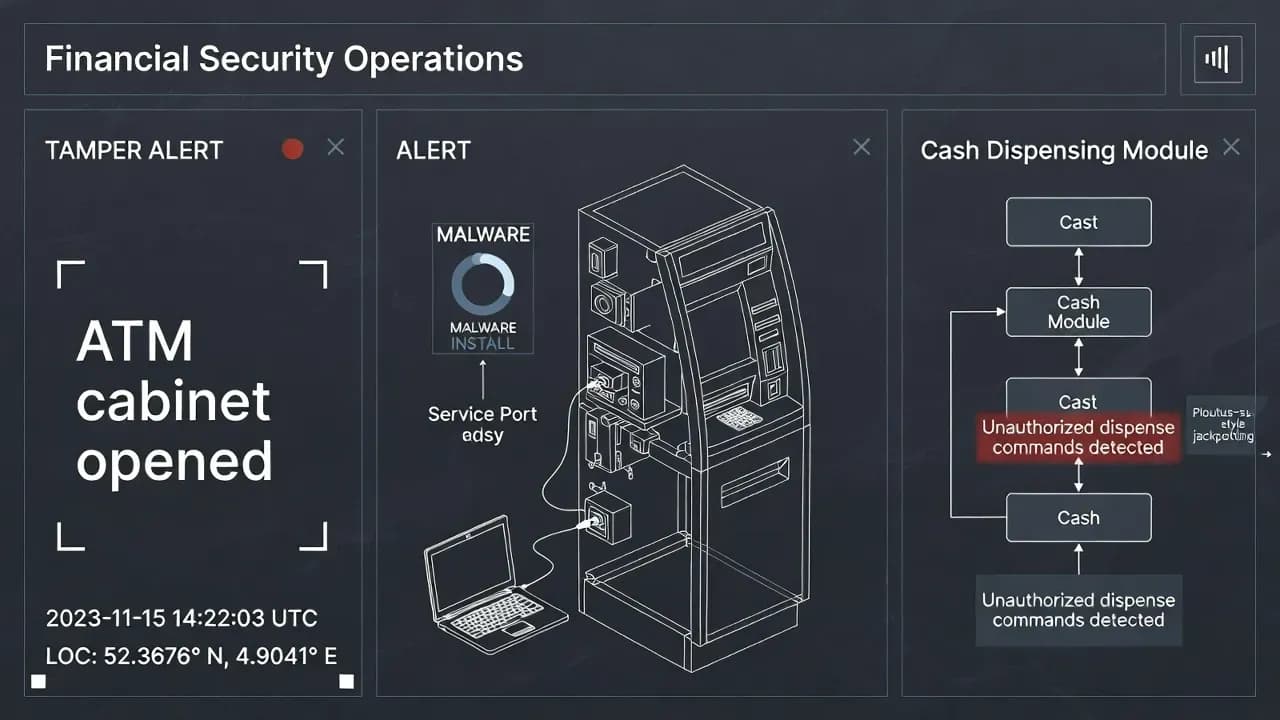
How ATM jackpotting works
ATM jackpotting is a physical-access attack that combines hardware manipulation with malware deployment.
Attack sequence
| Step | Action |
|---|---|
| 1. Physical access | Attacker gains access to ATM internals (lock picking, stolen keys, or exploiting poor physical security) |
| 2. Connection | Attacker connects to internal ports (USB, serial, or CD-ROM drive) |
| 3. Malware deployment | Ploutus or similar malware is installed, often by booting from external media |
| 4. Cash-out | Attacker or accomplice ("money mule") triggers cash dispensing via keyboard codes or external commands |
| 5. Extraction | Cash is collected, malware may be removed to avoid detection |
A skilled attacker can complete a jackpotting attack in under 15 minutes
Why Ploutus is effective
Ploutus was specifically designed for ATM environments:
- Targets Windows-based ATM platforms
- Interacts directly with the XFS (eXtensions for Financial Services) layer
- Can be controlled via keyboard commands or SMS (in some variants)
- Multiple versions targeting different ATM manufacturers
The Tren de Aragua connection
The involvement of Tren de Aragua highlights how traditional criminal organizations are adopting cyber techniques.
Organization profile
| Attribute | Detail |
|---|---|
| Origin | Tocorón prison, Aragua state, Venezuela |
| Expansion | Now operates across South America, Central America, and the United States |
| Activities | Extortion, human trafficking, drug trafficking, financial crimes, and increasingly cybercrime |
| U.S. designation | Designated as a Transnational Criminal Organization (TCO) |
Transnational criminal organizations are increasingly recruiting technical talent for cyber-enabled crimes
This case demonstrates the convergence of:
- Traditional organized crime (physical operations, money mules)
- Cybercrime techniques (specialized malware)
- Cross-border operations (evading jurisdictional boundaries)
Defensive measures for financial institutions
Organizations operating ATMs should implement layered defenses addressing both physical and software attack vectors.
Physical security controls
| Control | Implementation |
|---|---|
| Tamper-evident seals | Apply to all access panels; inspect regularly |
| Physical alarms | Alert on cabinet opening or vibration |
| CCTV coverage | Monitor all ATMs with adequate lighting and retention |
| Secure locations | Prioritize ATMs in staffed, well-lit areas |
| Key management | Strict control of maintenance keys; audit access logs |
Software hardening
| Control | Implementation |
|---|---|
| Application whitelisting | Only allow approved executables to run |
| Disable unused ports | USB, CD-ROM, and serial ports should be disabled in BIOS |
| Full-disk encryption | Protect against offline attacks |
| Secure boot | Prevent booting from external media |
| Regular patching | Keep ATM software and OS updated |
| Endpoint protection | Deploy ATM-specific security solutions |
Physical access prevention is the most effective control—if attackers cannot open the cabinet, software attacks become significantly harder
Detection and response
Warning signs of jackpotting
- Unusual ATM reboots or downtime
- Physical evidence of tampering (scratches, broken seals, residue)
- Anomalous cash dispensing patterns
- Error logs showing unauthorized software execution
- Reports of suspicious individuals near ATMs
Incident response steps
- Isolate - Take the ATM offline immediately
- Preserve - Do not reboot; preserve forensic evidence
- Report - Contact law enforcement and your ATM vendor
- Investigate - Review CCTV, access logs, and transaction records
- Analyze - Conduct forensic analysis of the ATM system
- Remediate - Address identified vulnerabilities before returning to service
Forensic evidence is critical for prosecution—improper handling can compromise criminal cases
Implications for the industry
This case has broader implications for financial sector security:
Immediate concerns
- Increased targeting: Successful prosecutions may temporarily deter, but jackpotting remains profitable
- Technique sharing: Malware and techniques spread through criminal networks
- Insider threats: Criminals may recruit ATM technicians or service personnel
Strategic considerations
| Factor | Implication |
|---|---|
| Aging ATM fleet | Older ATMs running Windows XP/7 are more vulnerable |
| Remote locations | Unattended ATMs in low-traffic areas are higher risk |
| Third-party servicers | Supply chain security extends to maintenance contractors |
| Insurance coverage | Review policies for jackpotting-specific coverage |
Conclusion
The conviction and deportation of Venezuelan nationals for Ploutus-based ATM jackpotting represents a law enforcement success, but the underlying threat persists. ATM jackpotting combines low technical barriers with potentially high payouts, making it attractive to both opportunistic criminals and organized groups.
Financial institutions should treat ATM security as a physical-plus-cyber problem, not just a software issue
Organizations operating ATMs should:
- Audit physical security at all ATM locations
- Implement software hardening including whitelisting and encryption
- Train staff to recognize tampering indicators
- Establish incident response procedures specific to jackpotting
- Share threat intelligence with industry peers and law enforcement
Frequently Asked Questions
ATM jackpotting is an attack where criminals gain physical access to an ATM, install malware or connect external devices, and force the machine to dispense all its cash on command. The term comes from the similarity to hitting a slot machine jackpot.
Ploutus is a specialized ATM malware family first discovered in 2013. It targets ATMs running Windows and allows attackers to dispense cash using keyboard commands or external triggers. Multiple variants have been observed targeting different ATM vendors.
Tren de Aragua is a Venezuelan transnational criminal organization that originated in the Aragua state prison system. It has expanded operations across Latin America and into the United States, engaging in various criminal activities including cybercrime, extortion, and human trafficking.
Attackers typically gain physical access by picking locks, using stolen maintenance keys, or exploiting weak physical security. They then connect to internal ports (USB, CD-ROM, or serial connections) to install malware or boot from external media.
Key defenses include physical security improvements (tamper-evident seals, alarms, CCTV), disabling unused ports, implementing whitelisting software, encrypting hard drives, regular security audits, and deploying ATM-specific endpoint protection.
Immediately take the ATM offline, preserve evidence, contact law enforcement and your ATM vendor, review surveillance footage, check for physical tampering signs, and conduct forensic analysis of the ATM software and logs.



Comments
Want to join the discussion?
Create an account to unlock exclusive member content, save your favorite articles, and join our community of IT professionals.
New here? Create a free account to get started.