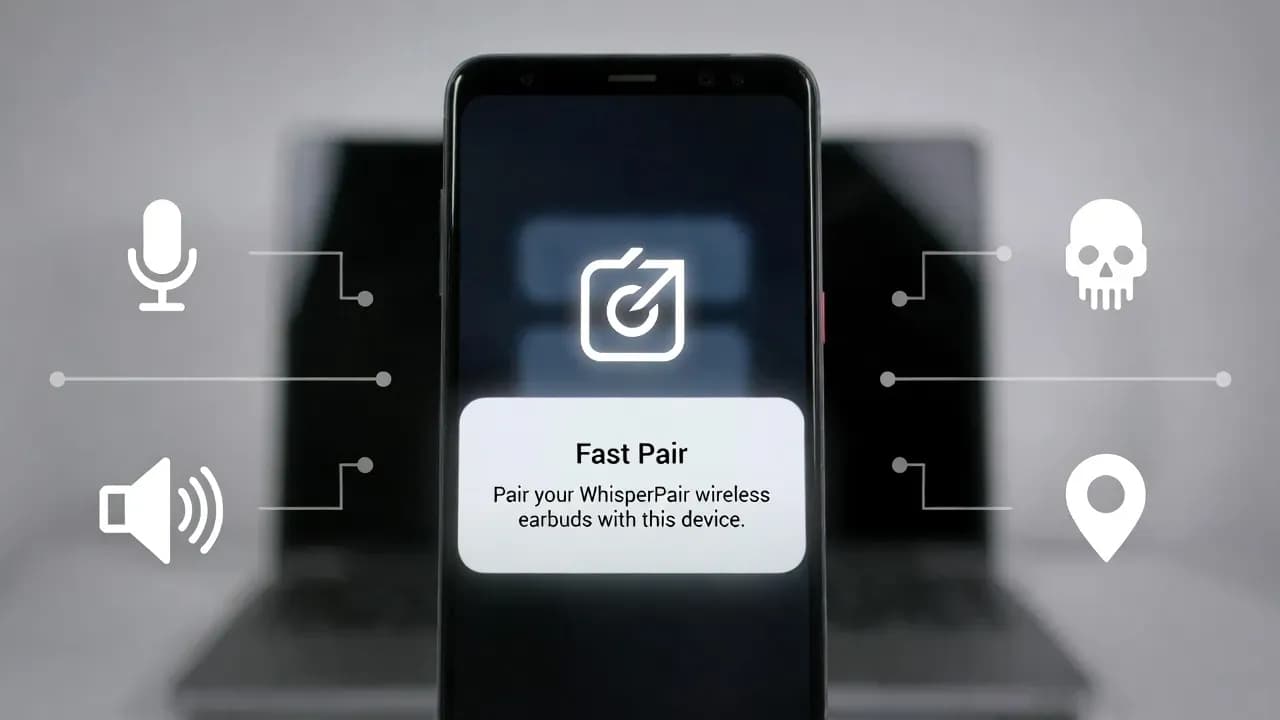
WhisperPair flaw hijacks Fast Pair earbuds for spying
WhisperPair is a critical Fast Pair implementation flaw affecting some Bluetooth earbuds, headphones, and speakers. Researchers show that an attacker in Bluetooth range can silently initiate a rogue pairing session, potentially taking over audio behavior and, in specific scenarios, abusing Find Hub to track a victim's location.
On January 15, 2026, KU Leuven researchers disclosed WhisperPair, a critical security issue that turns a convenience feature into a proximity threat. The WhisperPair Fast Pair vulnerability does not live in Android itself, and it is not a typical "update your phone" story. It targets how some Bluetooth audio accessories implement Google's Fast Pair workflow, which means the weak link is often the accessory firmware sitting in your pocket, on your desk, or in your ears.
Why it matters is simple: audio accessories are sensors and interfaces. They carry voice calls, ambient microphone input, and trusted audio output, and they increasingly integrate with location features like Find Hub. When attackers can silently trigger unauthorized pairing behavior within Bluetooth range, the result is not just a nuisance reconnection. It can become an eavesdropping risk, a disruption vector, or in specific edge cases, a location tracking primitive that follows the user rather than the phone.
What happened: the technical breakdown of the WhisperPair Fast Pair vulnerability
Fast Pair is designed to reduce friction by using Bluetooth Low Energy signaling and a guided workflow that helps a user pair an accessory quickly. The intended security boundary is that pairing is a deliberate act tied to device state. In practical terms, the accessory should behave differently when it is discoverable and in pairing mode versus when it is already paired and simply operating normally. That distinction is not cosmetic. It is supposed to prevent arbitrary nearby devices from initiating new pairing sessions whenever they want.
WhisperPair exists because many accessories fail to enforce a critical state check during the Fast Pair procedure. The researchers describe that Fast Pair begins when a "Seeker" sends a message to a "Provider" indicating it wants to pair. The Fast Pair specification expects providers to advertise and behave in specific ways depending on whether they are discoverable and in pairing mode, including how model identifiers and account data are broadcast. When accessories blur those boundaries, they can inadvertently permit unauthorized devices to start the pairing process even when a user never intended to pair anything.
The practical outcome is a class of proximity attacks: an attacker in Bluetooth range can silently initiate a pairing flow that should have been rejected, then proceed to establish control over the accessory's connection context. This is not about breaking Bluetooth encryption directly. It is about abusing implementation gaps in a higher-level pairing experience layered on top of Bluetooth, where "convenience first" behavior can become "authentication later" behavior.
What attackers can actually do: eavesdropping, audio takeover, and Find Hub tracking scenarios
The headline claims around WhisperPair can sound dramatic, so it is worth separating what is broadly possible from what depends on accessory capabilities. The baseline risk across vulnerable devices is unauthorized control over pairing and connection behavior. Once an attacker establishes their own pairing relationship, they can interfere with audio output, disrupt calls, or inject sound. Depending on the accessory design, this can be used for harassment, disorientation, or social engineering.
Eavesdropping is the sharper edge. Some accessories expose microphone functionality in ways that can be abused once a hostile pairing session exists. That does not automatically mean a Hollywood-style always-on remote mic for every model, but it does mean security teams should treat vulnerable accessories as potential listening surfaces in the wrong circumstances. In executive travel, journalism, legal work, and incident response war rooms, the mere uncertainty about whether a headset is behaving correctly is already damaging because it undermines trust in the environment.
The tracking angle is more specific but strategically important. Researchers also describe a scenario involving Find Hub where certain accessories can be linked to an attacker's Google account if the accessory was never previously associated with an Android device. In that case, the attacker can treat the accessory as "owned" and observe its location via the crowdsourced network, effectively tracking the user carrying it. The uncomfortable twist is that iPhone users are not insulated, because the vulnerability is in the accessory firmware and its Fast Pair behavior, not in the phone OS.
Affected organizations and industries: why this is bigger than consumer gadget hygiene
WhisperPair is a cybersecurity problem disguised as a consumer accessory story. The researchers and coverage emphasize that the issue can affect mainstream earbuds, headphones, and speakers across multiple brands, which implies two operational realities:
- The exposure surface is wide because accessories are commodity products purchased outside of IT
- Patching is inconsistent because accessory firmware updates are often distributed through vendor apps, and many users never install them
For enterprises, this collides directly with modern work patterns. Contact centers rely on headsets all day. Executives travel with premium earbuds. Remote workers use whatever they own, switching between personal and corporate devices in the same week. Yet very few organizations inventory audio accessories, validate firmware, or define what "approved" even means.
The threat model is also practical. WhisperPair is a proximity attack, which means it thrives in exactly the places enterprise users operate: airports, trains, conferences, lobbies, co-working spaces, and coffee shops. The attacker does not need internet exposure to the victim. They need short-range access, brief time, and the right target conditions.
Key numbers at a glance
Vulnerable models confirmed in the research set
Companies represented in the confirmed vulnerable set
Tested takeover time in demonstrations
Tested hijack distance (about 46 feet)
| Field | Value |
|---|---|
| Vulnerable models | 17 audio accessories |
| Vendors affected | 10 companies |
| Takeover time | 10 to 15 seconds |
| Attack distance | ~14 meters (46 feet) |
| Initial disclosure | August 2025 |
Source verification map
- 17 accessories, 10 companies, Bluetooth range, takeover time, disclosure timing: source [1], source [2].
What to do next: mitigation, patching, and enterprise policy that actually works
The most important mitigation is also the least glamorous: update accessory firmware. WhisperPair cannot be meaningfully "fixed" by updating the phone alone, and factory resets do not address the underlying implementation flaw. If an accessory is vulnerable, only the manufacturer's firmware update changes the behavior that enables the attack.
For IT and security teams, the response should be staged:
- Identify whether Fast Pair accessories are common in your environment
- Query purchase history if you have procurement control
- Run an internal survey targeting high-risk roles to identify which models dominate
- Create an update campaign that treats headsets like patchable assets
- Provide clear instructions for the top few models
Policy should focus on risk reduction rather than perfection:
- Discourage accessory use in high-risk physical locations
- Require users to disable Bluetooth when not needed
- Train support teams to recognize suspicious behaviors (repeated pairing prompts, unexplained disconnects, sudden audio routing changes)
- For new accessories, establish ownership and pairing intentionally as early as possible
- For sensitive teams, issue managed accessories with a controlled update path
Lessons learned: convenience protocols and certification need security-by-design
WhisperPair highlights an industry pattern that repeats across IoT, wearables, and peripherals: usability layers tend to outpace security discipline. Fast Pair is not "broken Bluetooth." It is a convenience protocol that depends on correct implementation across chip suppliers, firmware stacks, and accessory vendors. The researchers argue that relying on state checks alone is fragile and propose binding pairing intent more cryptographically so that the security property is enforced by design rather than assumed by convention.
There is also a certification lesson. Vendor ecosystems often use validator tooling and lab testing to prove compliance, but WhisperPair shows that compliant user experience does not necessarily imply resilient security behavior in edge cases. When a protocol is widely deployed and marketed across 60-plus brands, even a small implementation ambiguity can create systemic risk.
Closing
WhisperPair is a reminder that modern security perimeters include the things people wear and carry, not just the endpoints IT owns. When an accessory-level convenience protocol can be abused from Bluetooth range, the practical risk is not limited to tech enthusiasts. It touches hybrid work, executive travel, and any environment where private conversations happen on commodity headsets.
The most effective response is straightforward: identify affected accessories and push firmware updates aggressively. The longer-term fix is cultural and architectural: treat peripherals as patchable devices with ownership, firmware, and lifecycle expectations. WhisperPair is unlikely to be the last story in this category. It is a signal that accessory security has matured into a first-class enterprise concern.
Frequently Asked Questions
No. The weakness is in how some accessories implement Fast Pair behavior, not in the phone OS. Updating your phone is still good hygiene, but it does not fix a vulnerable accessory firmware implementation.
Yes. If the accessory is vulnerable, the attack targets the accessory's Fast Pair implementation, so iPhone users can still be impacted.
You can disable Fast Pair scanning prompts on some Android devices, but that does not remove Fast Pair support from the accessory itself. The recommended mitigation is firmware updating the accessory.
No. A reset can clear pairings, but it does not fix the underlying vulnerability. The accessory still needs a firmware update.
In specific cases, if an accessory has never been linked to an Android device account, an attacker can abuse the pairing weakness to associate it with their own account, then use Find Hub location reporting to track it.




Comments
Want to join the discussion?
Create an account to unlock exclusive member content, save your favorite articles, and join our community of IT professionals.
New here? Create a free account to get started.