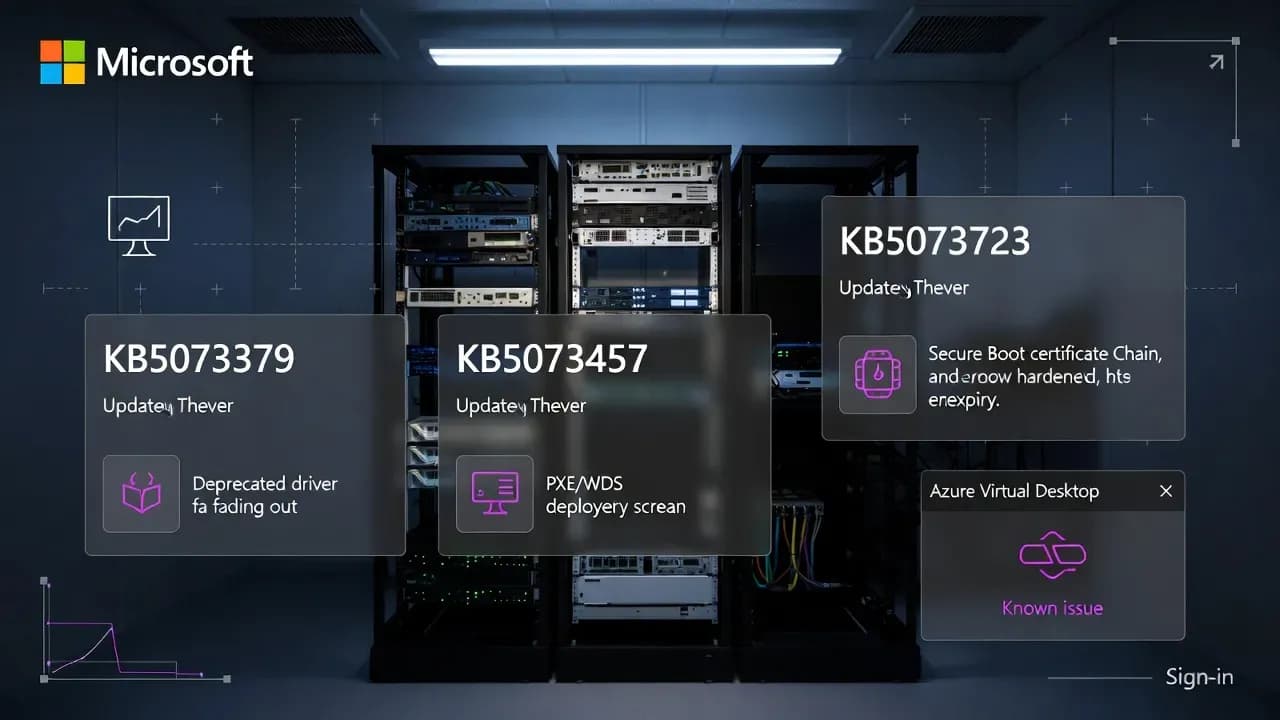
Windows Server January 2026 updates: KB5073379 (Server 2025), KB5073457 (Server 2022), KB5073723 (Server 2019)
Microsoft's January 2026 Patch Tuesday delivers new cumulative updates for Windows Server 2025, 2022, and 2019, including WDS hardening changes tied to CVE-2026-0386, driver removals for CVE-2023-31096, and a known issue impacting Azure Virtual Desktop and Windows 365 sign-ins via Windows App.
Microsoft's first Patch Tuesday of 2026 shipped on January 13, 2026, with new cumulative updates for Windows Server across supported LTSC versions. The headline is simple: Server 2025 now has its own KB numbering, WDS hardening work continues (with real deployment impact), and Microsoft is also pushing foundational security maintenance such as Secure Boot certificate lifecycle handling.
This roundup focuses on what changed in the January 2026 "B" release and the practical validation steps you can run in enterprise environments.
At a glance: KBs and builds for January 2026
| Platform | January 2026 KB | Build | Notes |
|---|---|---|---|
| Windows Server 2025 (LTSC) | KB5073379 | 26100.32230 | Server 2025 now uses its own KB identifiers |
| Windows Server 2022 (LTSC) | KB5073457 | 20348.4648 | Includes a Citrix-related SearchIndexer fix |
| Windows Server 2019 (LTSC) | KB5073723 | 17763.8276 | Includes WDS hardening changes and driver removals |
| Windows Server 2016 (LTSB) | KB5073722 | 14393.8783 | Same core themes as Server 2019 (per recap) |
The shared themes across Server 2025, 2022, and 2019
1) Driver removals to mitigate CVE-2023-31096 (Agere modem drivers)
A notable operational change: Microsoft removed multiple legacy Agere modem drivers to address CVE-2023-31096. If you still have hardware or virtual modem dependencies (rare, but not impossible in industrial and legacy deployments), this can become a surprise outage after patching.
What to validate:
- Inventory systems that depend on these legacy drivers (if any exist in your estate).
- After patching, confirm no unexpected device failures in niche comms stacks.
2) WDS hardening tied to CVE-2026-0386 (hands-free deployment impact)
If you run Windows Deployment Services (WDS), January 2026 is a milestone month. Microsoft is phasing out insecure "hands-free" workflows by default as part of hardening guidance related to CVE-2026-0386. The practical takeaway is that unattended imaging patterns can be impacted, especially where answer files and legacy behaviors are assumed.
What to validate:
- Confirm whether your WDS flow relies on hands-free behavior and unattend.xml patterns.
- Read Microsoft's hardening guidance and plan your deployment workflow changes (this is not just a patch, it is a process change).
3) WinSqlite3.dll component refresh
Microsoft updated WinSqlite3.dll, noting that some security products previously flagged the component as vulnerable. This is low drama, but it is the kind of change that can reduce false positives in certain endpoint security stacks.
What to validate:
- Watch EDR/AV telemetry for reduced noisy detections around WinSqlite3.dll after patching.
Windows Server 2025: KB5073379 highlights you should care about
Server 2025 now has its own KB identifiers
Starting with this January 2026 update, Windows Server 2025 updates get dedicated KB IDs, instead of sharing identifiers with Windows 11 (24H2/25H2). This is a meaningful improvement for patch governance, reporting, and WSUS/Intune ring clarity.
RemoteApp reliability fix for Azure Virtual Desktop environments
KB5073379 includes a fix for RemoteApp connection failures in Azure Virtual Desktop that could appear after installing KB5070311 (December 2025). For orgs that use published apps instead of full desktops, this is a high-value stability improvement.
Hotpatch servicing edge case resolved (for some OOB scenarios)
Microsoft also addresses a scenario where servers that installed an earlier out-of-band update could fail to receive Hotpatch updates until the base January update is installed. If you are running Hotpatch and maintain emergency OOB history, this is worth confirming.
Secure Boot certificate lifecycle work
Microsoft is also preparing distribution of new Secure Boot certificates, driven by 2026 expirations. Even if this is "behind the scenes," it touches the trust chain for boot integrity and should be treated as a change you track in regulated environments.
Known issue: Windows App sign-in failures for AVD / Windows 365
There is a known issue where Remote Desktop authentication via Windows App can fail when connecting to Azure Virtual Desktop or Windows 365. Microsoft's guidance points admins to use the Remote Desktop app or the web client as the immediate workaround.
What to validate:
- If your users connect via Windows App, test sign-in to AVD/Windows 365 in a pilot ring before broad rollout.
- Ensure your service desk has a documented fallback path (Remote Desktop app or web).
Windows Server 2022: KB5073457 includes a Citrix-host fix
Beyond the shared changes (drivers, WDS hardening trajectory, WinSqlite3.dll update), Microsoft also notes a fix where SearchIndexer could stop on Citrix hosts, which may block users from starting remote sessions in some environments.
What to validate:
- For Citrix-hosted workloads, verify session launch reliability after patching.
- Monitor SearchIndexer stability and any correlated log patterns that previously matched your incident history.
Windows Server 2019: KB5073723 keeps the focus on deployment hardening
For Server 2019, Microsoft emphasizes the same three practical changes:
- Agere modem driver removals tied to CVE-2023-31096
- WDS hardening direction (hands-free deployment behavior changes)
- WinSqlite3.dll updated
If you have long-lived imaging pipelines built around Server 2019, the WDS angle is the one most likely to create operational surprises.
Suggested admin checklist for this month
- Patch and record: Ensure you map KB-to-build per OS so you can answer "what's installed" instantly during incident response.
- Validate WDS: If you use WDS, treat January 2026 as the start of a controlled migration away from hands-free assumptions.
- Test AVD/Windows 365 connectivity: Especially if Windows App is the default client in your org.
- Watch for legacy driver dependencies: Rare, but worth a quick sanity check in any environment with old peripherals or industrial integrations.
- Monitor security tooling noise: WinSqlite3.dll changes can shift detection behavior.
Frequently Asked Questions
Windows Server 2025, 2022, and 2019 received January 13, 2026 cumulative updates (KB5073379, KB5073457, KB5073723). A related update also shipped for Windows Server 2016 (KB5073722).
For many enterprises, the WDS hardening direction tied to CVE-2026-0386 is the most likely to affect deployment workflows, especially where hands-free and unattended imaging patterns are still used.
Microsoft removed several Agere modem drivers to mitigate CVE-2023-31096. Systems that still depend on those legacy drivers may experience device functionality loss after patching.
Microsoft documents credential prompt failures when using Windows App to connect to Azure Virtual Desktop or Windows 365 after installing KB5073379. Workarounds include using the Remote Desktop app or the web client.
Yes. Microsoft notes KB5073457 resolves an issue where SearchIndexer could stop on Citrix hosts, which could prevent users from starting remote sessions.


Comments
Want to join the discussion?
Create an account to unlock exclusive member content, save your favorite articles, and join our community of IT professionals.
New here? Create a free account to get started.