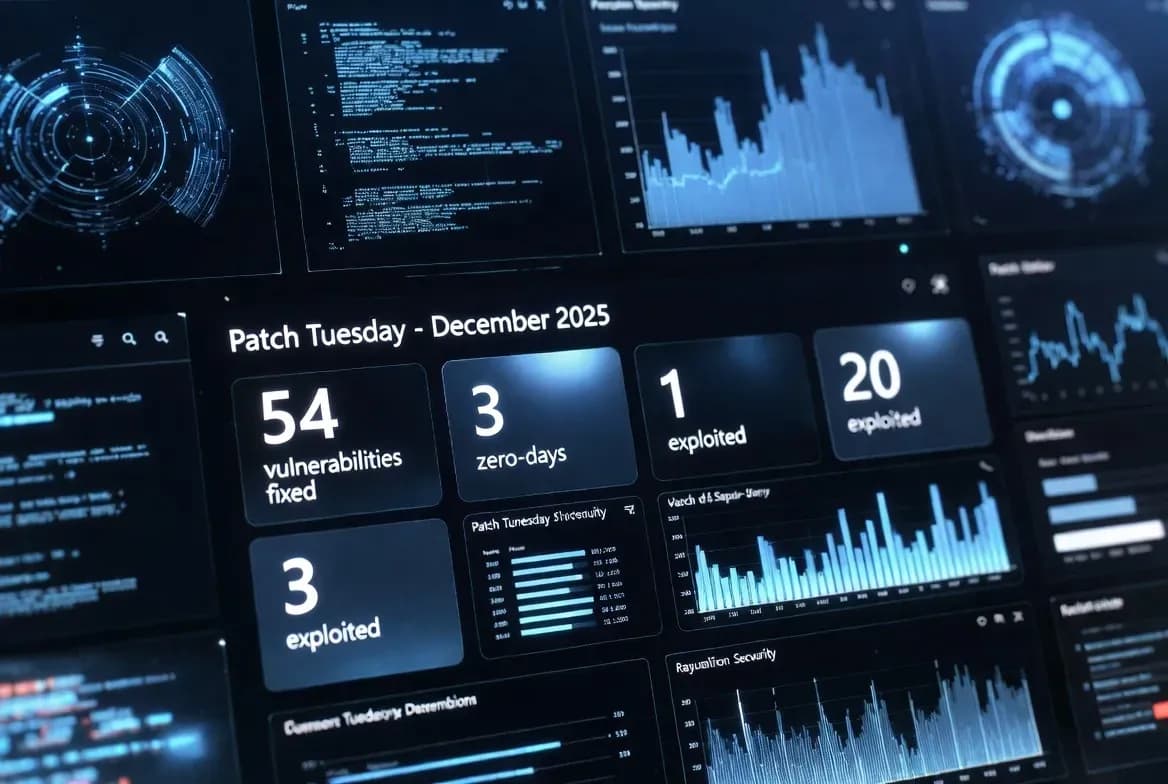
Microsoft Patch Tuesday – December 2025: Critical Zero-Days, Windows and Exchange in Focus
Microsoft’s December 2025 Patch Tuesday delivers a high-impact security update addressing multiple critical vulnerabilities across Windows, Windows Server, Exchange, and Microsoft 365. Several actively exploited zero-days raise immediate patching urgency for enterprise and cloud environments.
Executive Summary
Microsoft’s December 2025 Patch Tuesday marks one of the most security-sensitive update cycles of the year. This release addresses dozens of vulnerabilities across Windows, Windows Server, Microsoft 365, and Exchange, including multiple zero-day flaws confirmed as actively exploited in the wild.
The update is particularly critical for organizations operating hybrid identity infrastructures, on-premises Exchange deployments, and internet-exposed Windows services. Several vulnerabilities affect core authentication mechanisms, directory services, and network-facing components, increasing the risk of lateral movement and privilege escalation within enterprise environments.
Microsoft strongly recommends immediate deployment for systems exposed to the internet or handling sensitive authentication workloads.
What Changed
The December 2025 Patch Tuesday introduces a broad set of security fixes across Microsoft’s ecosystem, with a clear focus on remote code execution (RCE) and elevation of privilege (EoP) vulnerabilities.
Key security changes include strengthened protections in Windows authentication and directory services, as well as multiple fixes targeting network-accessible Windows components commonly abused by threat actors.
Critical updates were also released for Microsoft Exchange Server, addressing attack vectors frequently leveraged in ransomware and espionage campaigns. In addition, Microsoft 365 services received security hardening to reinforce cloud and hybrid security boundaries.
No major user-facing features are introduced in this cycle. The update is almost entirely focused on risk mitigation, exploit prevention, and enterprise security stability.
Security Analysis Security researchers have confirmed that at least two vulnerabilities patched in this release were actively exploited prior to update availability. These zero-day flaws allowed attackers to elevate privileges or execute code remotely under specific conditions.
Of particular concern are vulnerabilities affecting:
- Windows Server roles exposed to external networks
- Active Directory - related authentication services
- Exchange Server components historically targeted by advanced threat groups
The presence of actively exploited zero-days significantly increases the risk profile of unpatched systems. Attackers leveraging these vulnerabilities could bypass security controls, escalate privileges, and establish persistent access inside enterprise environments.
Organizations following delayed or quarterly patching strategies should reassess their exposure immediately.
Who Should Update This update is critical for the following environments:
- Enterprises running Windows Server in internet-facing or hybrid deployments
- Organizations maintaining on-premises Microsoft Exchange Server
- Businesses using Microsoft 365 with hybrid identity synchronization
- Managed Service Providers (MSPs) responsible for multi-tenant Windows infrastructures
Even systems not directly exposed to the internet remain at risk due to post-exploitation lateral movement techniques once an attacker gains an initial foothold.
Deployment Guidance
For Windows clients and servers, updates should be deployed via Windows Update, WSUS, or Microsoft Endpoint Manager (Intune) as soon as possible.
Recommended deployment approach
- Prioritize internet-facing servers, domain controllers, and identity infrastructure
- Apply updates in a staged rollout for business-critical production systems
- Monitor authentication logs, endpoint telemetry, and security alerts post-deployment
- Validate Exchange Server services, mail flow, and authentication after patch installation
Organizations relying on custom authentication extensions, legacy protocols, or third-party integrations should validate compatibility before large-scale rollout.
Conclusion
Microsoft’s December 2025 Patch Tuesday stands out as one of the most security-critical update cycles of the year. The combination of actively exploited zero-day vulnerabilities, high-impact fixes affecting Windows and Exchange, and the breadth of affected enterprise environments leaves little room for delayed action.
For organizations operating hybrid identity infrastructures, internet-facing servers, or legacy on-premises Exchange deployments, this update should be treated as a top-tier security priority. The risk of credential compromise, lateral movement, and service disruption remains significant until all affected systems are fully patched and validated.
Beyond immediate remediation, this release reinforces a broader trend: modern attacks increasingly target identity services, directory infrastructure, and authentication flows rather than isolated endpoints. As such, Patch Tuesday should not be viewed as a routine maintenance task, but as an opportunity to reassess exposure, monitoring capabilities, and patch governance processes.
Timely deployment, post-update validation, and continuous monitoring will remain essential to maintaining a resilient Windows and Microsoft 365 security posture going into 2026.
Related Updates
View All
RIP MDT: Microsoft Quietly Kills Its Free Windows Deployment Toolkit
After nearly 20 years, Microsoft has silently discontinued the Microsoft Deployment Toolkit (MDT), removing downloads an...

Classic Outlook Bug Blocks Opening Encrypted Emails from External Organizations
Microsoft confirms a known issue preventing Classic Outlook users from opening OMEv2 encrypted emails sent from other Mi...

Microsoft Cancels Exchange Online Bulk Email Limits After Customer Backlash
Microsoft has abandoned its controversial plan to limit Exchange Online mailboxes to 2,000 external recipients per day....
Comments
Want to join the discussion?
Create an account to unlock exclusive member content, save your favorite articles, and join our community of IT professionals.
New here? Create a free account to get started.